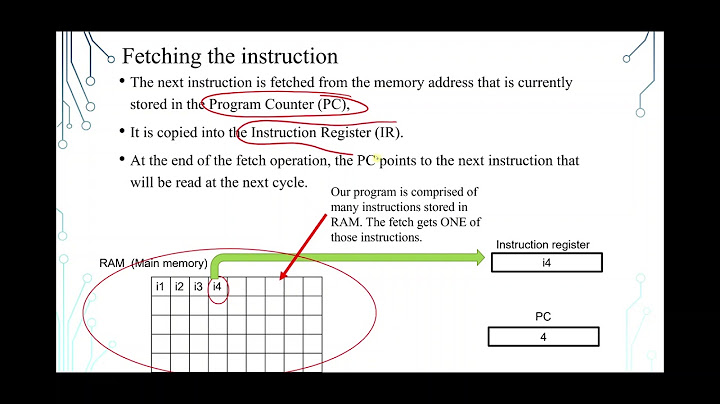
Background LAN Manager (LM) authentication is the protocol that is used to authenticate Windows clients for network operations, including domain joins, accessing network resources, and user or computer authentication. The LM authentication level determines which challenge/response authentication protocol is negotiated between the client and the server computers. Specifically, the LM authentication level determines which authentication protocols that the client will try to negotiate or that the server will accept. The value that is set for LmCompatibilityLevel determines which challenge/response authentication protocol is used for network logons. This value affects the level of authentication protocol that clients use, the level of session security negotiated, and the level of authentication accepted by servers. Possible settings include the following.
Note In Windows 95, Windows 98, and Windows 98 Second Edition, the Directory Services Client uses SMB signing when it authenticates with Windows Server 2003 servers by using NTLM authentication. However, these clients do not use SMB signing when they authenticate with these servers by using NTLMv2 authentication. Additionally, Windows 2000 servers do not respond to SMB signing requests from these clients. Check the LM authentication level: You must change the policy on the server to permit NTLM, or you must configure the client computer to support NTLMv2. If the policy is set to (5) Send NTLMv2 response only\refuse LM & NTLM on the target computer that you want to connect to, you must either lower the setting on that computer or set the security to the same setting that is on the source computer that you are connecting from. Find the correct location where you can change the LAN manager authentication level to set the client and the server to the same level. After you find the policy that is setting the LAN manager authentication level, if you want to connect to and from computers that are running earlier versions of Windows, lower the value to at least (1) Send LM & NTLM - use NTLM version 2 session security if negotiated. One effect of incompatible settings is that if the server requires NTLMv2 (value 5), but the client is configured to use LM and NTLMv1 only (value 0), the user who tries authentication experiences a logon failure that has a bad password and that increments the bad password count. If account lock-out is configured, the user may eventually be locked out. For example, you may have to look on the domain controller, or you may have to examine the domain controller's policies. Look on the domain controller Note You may have to repeat the following procedure on all the domain controllers.
If the Effective Setting and the Local Setting are the same, the policy has been changed at this level. If the settings are different, you must check the domain controller's policy to determine whether the Network Security: LAN manager authentication level setting is defined there. If it is not defined there, examine the domain controller's policies. Examine the domain controller's policies
Windows Server 2003 has a new default setting to use NTLMv2 only. By default, Windows Server 2003 and Windows 2000 Server SP3-based domain controllers have enabled the "Microsoft network server: Digitally sign communications (always)" policy. This setting requires the SMB server to perform SMB packet signing. Changes to Windows Server 2003 were made because domain controllers, file servers, network infrastructure servers, and Web servers in any organization require different settings to maximize their security. If you want to implement NTLMv2 authentication in your network, you must make sure that all the computers in the domain are set to use this authentication level. If you apply Active Directory Client Extensions for Windows 95 or Windows 98 and Windows NT 4.0, the client extensions use the improved authentication features that are available in NTLMv2. Because client computers that are running any of the following operating system are not affected by Windows 2000 Group Policy Objects, you may have to manually configure these clients:
Note If you enable the Network security: Do not store LAN manager hash value on next password change policy or set the NoLMHash registry key, Windows 95-based and Windows 98-based clients that do not have the Directory Services Client installed cannot log on to the domain after a password change. Many third-party CIFS servers, such as Novell Netware 6, are not aware of NTLMv2 and use NTLM only. Therefore, levels greater than 2 do not permit connectivity. There also are third-party SMB clients that do not use extended session security. In these cases, the LmCompatiblityLevel of the resource server is not taken into consideration. The server then packs up this legacy request and sends it to the User Domain Controller. The settings on the Domain Controller then decide what hashes are used to verify the request and whether these are meeting the Domain Controller's security requirements. For more information about how to manually configure the LAN manager authentication level, click the following article numbers to view the articles in the Microsoft Knowledge Base: 147706 How to disable LM authentication on Windows NT 299656 How to prevent Windows from storing a LAN manager hash of your password in Active Directory and local SAM databases 312630 Outlook continues to prompt you for logon credentials 2701704Audit event shows authentication package as NTLMv1 instead of NTLMv2 For more information about LM authentication levels, click the following article number to view the article in the Microsoft Knowledge Base: 239869 How to enable NTLM 2 authentication Risky configurations The following are harmful configuration settings:
Reasons to Modify This Setting
Reasons to disable this setting Client or server authentication requirements, or both, have been increased to the point where authentication over a common protocol cannot occur. Symbolic Name: LmCompatibilityLevel Registry Path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\LmCompatibilityLevel Examples of compatibility problems
|

zusammenhängende Posts
Werbung
NEUESTEN NACHRICHTEN
Toplisten
#1
#2
#3
Top 8 zeichnen lernen für kinder online 2022
2 Jahrs vor#4
Top 8 schluss machen trotz liebe text 2022
2 Jahrs vor#5
#6
Top 8 wie fallen calvin klein sneaker aus 2022
1 Jahrs vor#7
Top 5 mi band 3 schrittzähler einstellen 2022
1 Jahrs vor#8
#9
Top 9 sich gegenseitig gut tun englisch 2022
2 Jahrs vor#10
Werbung
Populer
Werbung

Urheberrechte © © 2024 wiewird Inc.